ELEZAR
Relevant Threat Intelligence.
Zero Overhead.
Know what to do against your most relevant threats, instantly. Join the Q4 2025 launch.
Benefits
Accelerate Threat-Informed Outcomes.
zero overhead
Our platform continuously collects, curates and analyses thousands of open-source intelligence reports from across the global security landscape.
No feeds to configure.
No sources to maintain.
No engineering overhead.
relevance on demand
Cut through the noise with Constellations™ - an innovative way to continuously track, filter and visualize the world's intelligence to match the your most relevant threats.
Define relevance based on the following and many more attributes:
Geographic regions under your protection
Industry sectors you or your customers operate in
Specific technologies relevant to your stack
Make threats make sense
Turn raw adversary behavior into clear, prioritized stories for your team and stakeholders using:
MITRE ATT&CK Heat-maps to prioritize detection, hunt and mitigation focus.
Attack Path visualizations - realistic journeys you can test, defend, and explain.
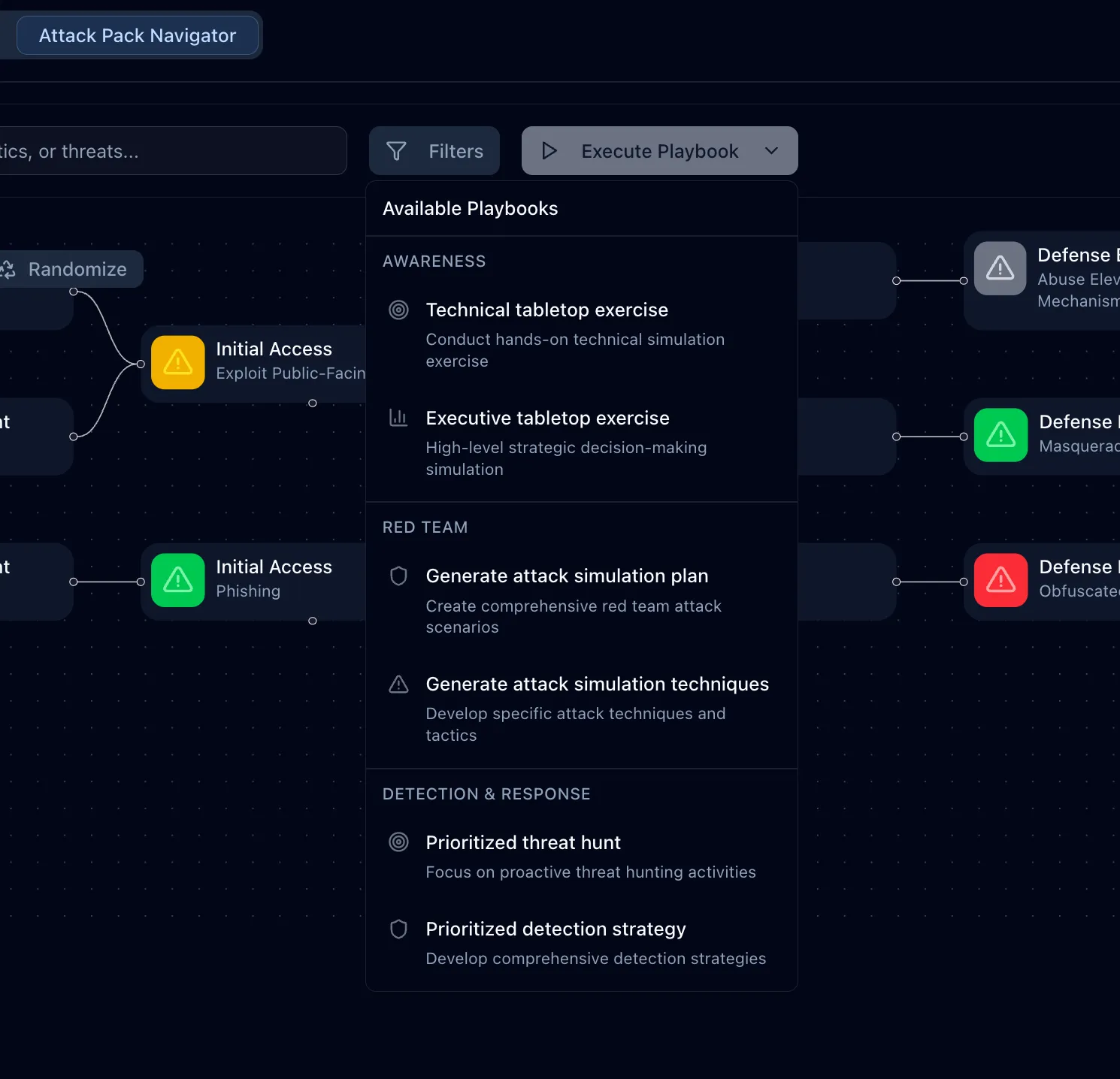
execute threat-informed playbooks
Go from insight to action instantly with repeatable, evidence-based playbooks for defensive, offensive and executive stakeholders at the click of a button.
Prioritized hunting guidelines and detection analytics
Attack simulation plans and execution guidelines
Executive or technical tabletop scenarios
Your Time is Limited. Your Threats Aren't. Focus on What Matters.
COMPARISON
Different by Design.
Traditional Threat Intelligence Platforms
Elezar
Deployment
Heavy setup, high overhead
Cloud-native, instant access
Operational Focus
Deliver intelligence but demand dedicated teams to make it useful
Turns intelligence into outcomes at the click of a button
Intelligence
Feeds & raw data
Curated, finished open-source threat intelligence research
Relevance
Generic
Constellations™ - customized threat focus
MITRE ATT&CK
Static or Manual mapping
Evidence-based heat maps that drive defensive, offensive or risk prioritization
Analysis
Dependant on feeds or analyst capacity
Every report analysed, attributed and mapped to MITRE ATT&CK
AI Implementation
Bolt-on addition
AI embedded architecture & design
Cost
Enterprise-only pricing
Freemium + scalable tiers
Usability
Analyst & Engineering experience required
Outcomes without specialized skills
Visuals
Generic dashboards
Clear heat maps & attack paths
Features
Threat Intelligence with Purpose.
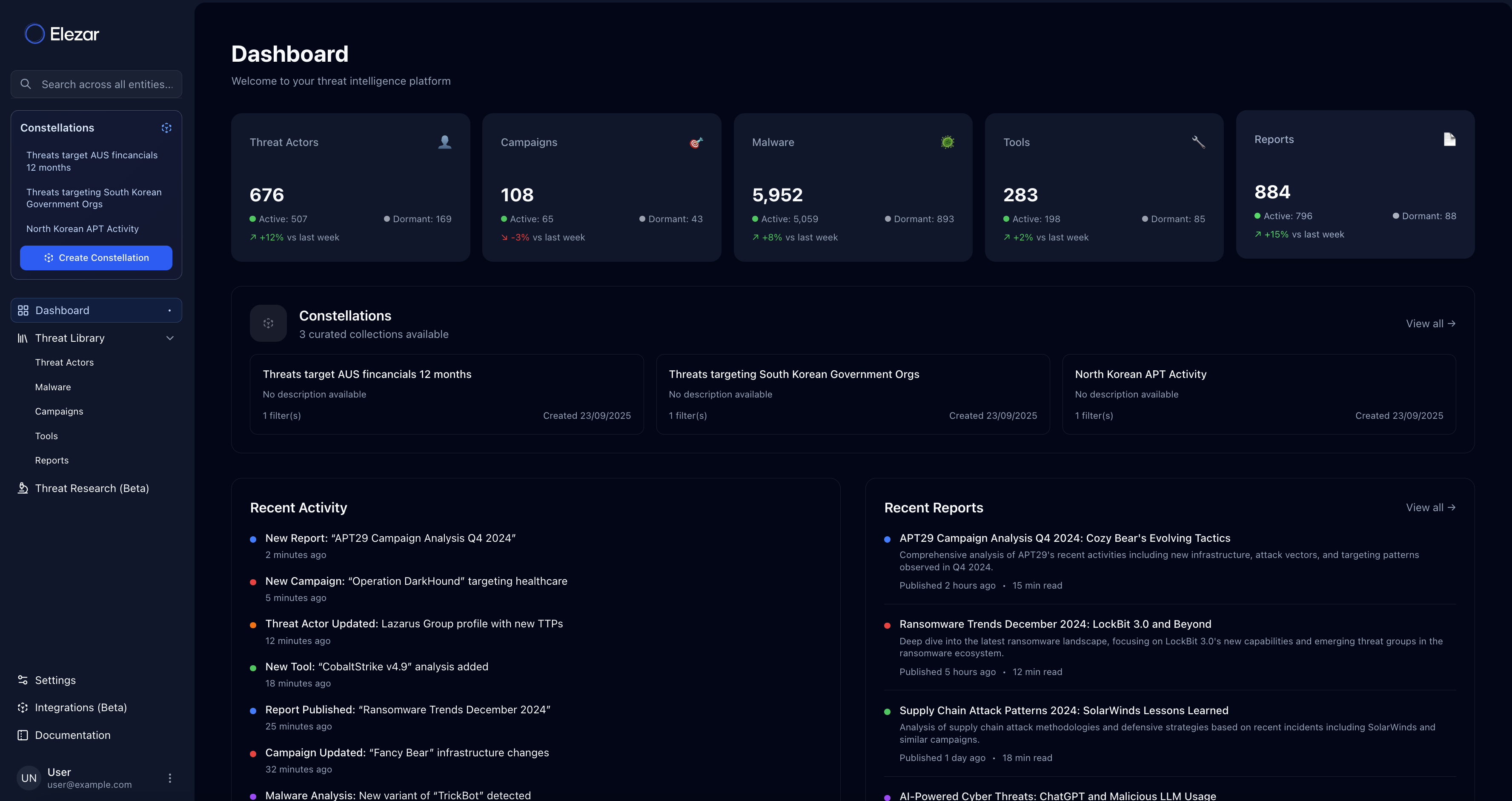
Freemium Threat Library. Search everything. Find what matters.
Research a galaxy of intelligence: thousands of curated threat actors, malware families, campaigns, reports and more - all mapped to the MITRE ATT&CK framework.
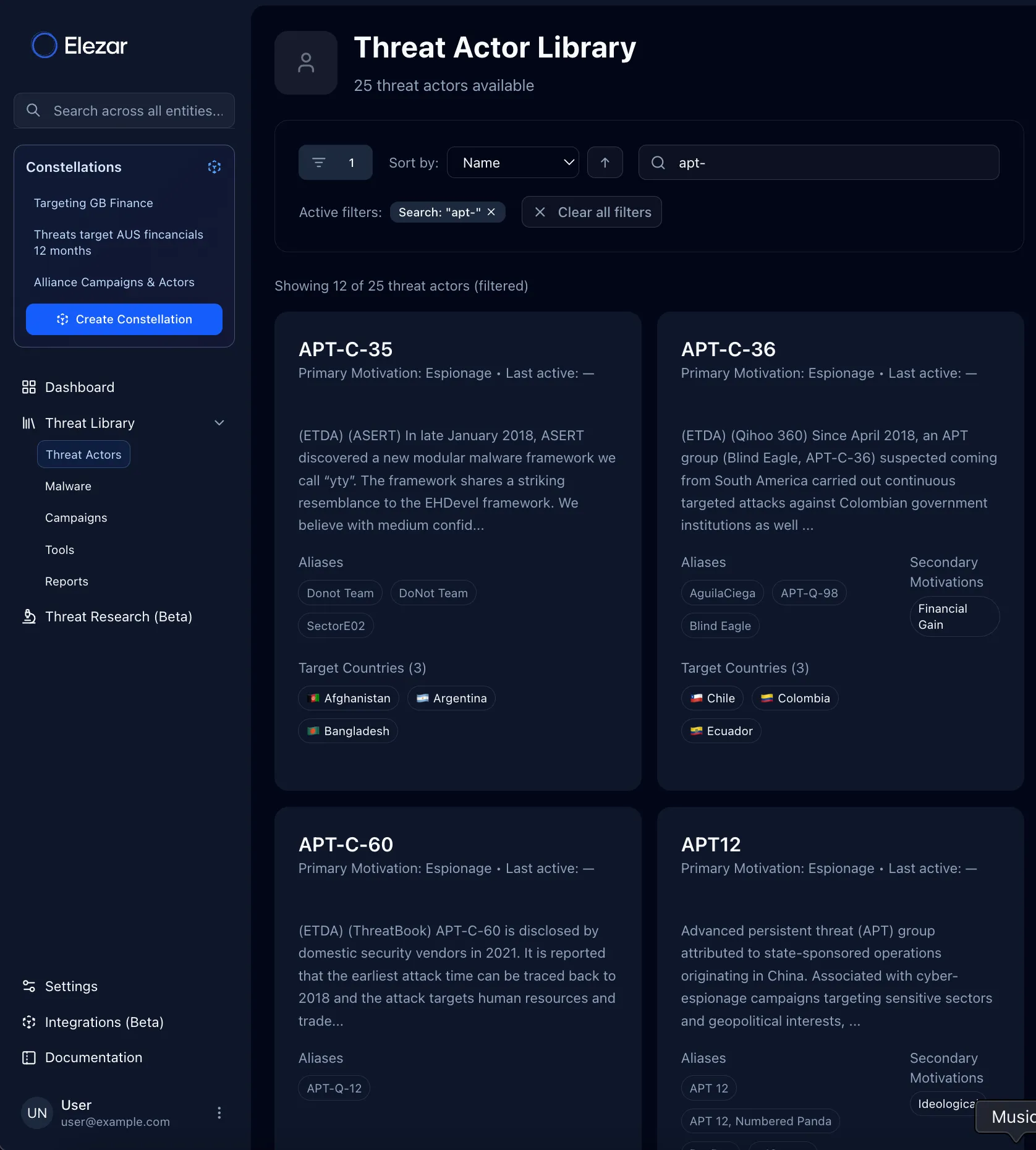
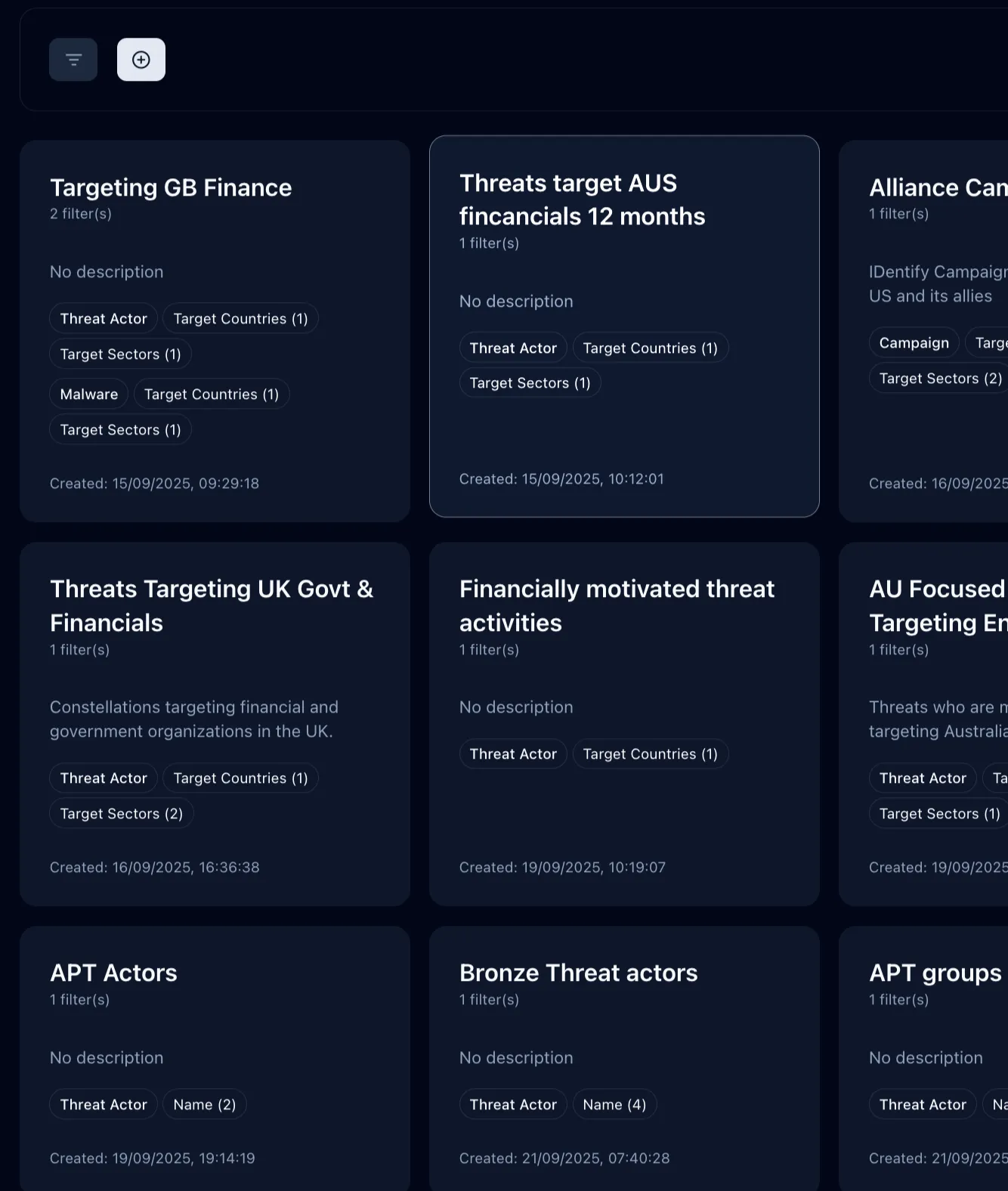
Constellations™ - Your intelligence, your way.
Stop drowning in global noise. Create custom views that track, filter and view only the threats relevant to your organization. Set it once, stay informed forever.
Because intelligence worth your attention should find you, not the other way around.
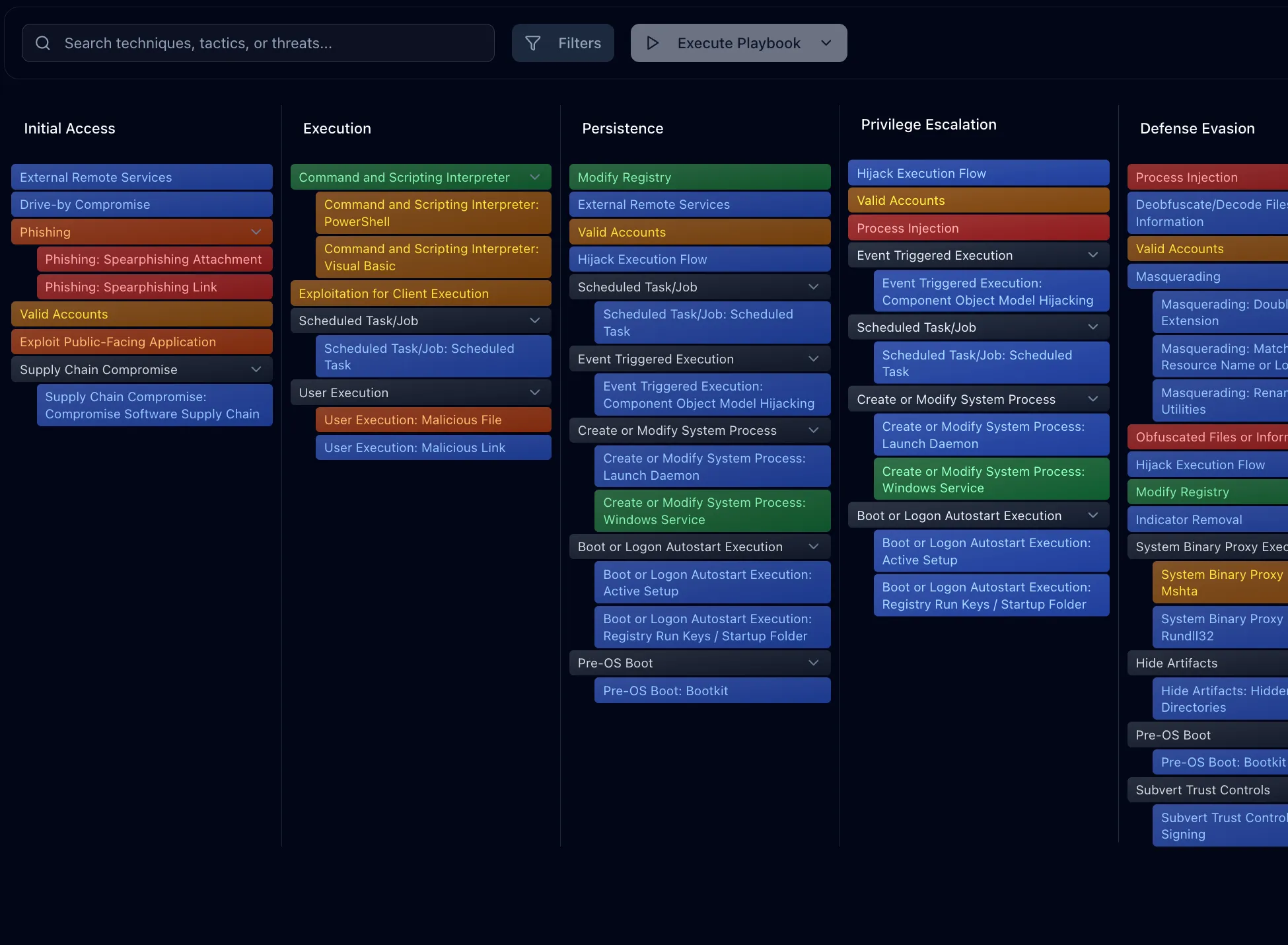
Evidence-Based MITRE ATT&CK. See the proof behind every technique.
Every ATT&CK technique is backed by the exact source report where techniques were observed. Click any technique within the platform to see exactly where it was observed - down to the page.
No assumptions. No guesswork. Just defensible intelligence
Attack Path Navigator. Visualize attacks before they happen.
Pivot from MITRE ATT&CK and visualize how real-world adversaries could move through your environment. Plan red team scenarios, validate defenses, and tell the story of risk in a way that makes sense to both analysts and executives.
See the path. Stop the threat.

Execute Playbooks. Maximizing threat-informed outcomes.
Execute Playbooks transforms adversary insights into tabletop exercises, simulations, and defensive playbooks you can run today.
From insight to execution in one step. Playbooks convert evidence-driven intelligence into repeatable workflows your team can act on instantly.
The Process
Threat-led Outcomes in Under 5 Minutes
01
Sign Up For Free
Create your account in seconds. No credit card. No complex setup. Just immediate access to intelligence worth your attention.
02
Create your Constellation™
Tell us what matters: your industry, geography, technologies, threat adversaries. Watch as Elezar instantly filters thousands of reports to show only relevant threats.
03
Execute Playbooks
Transforms your most relevant threats and adversary insights into tabletop exercises, attack simulations, and defensive measures.
This is how threat intelligence should work - automated, relevant, and outcome focused.
Pricing
Pricing That Respects Your Journey
Freemium
Perfect for individual analysts exploring better intelligence.
Features
Full threat library access
Basic search
Lite
Perfect for security professionals who want deeper Tactic, Technique and Procedural (TTP) understanding and visualisations.
Features
Everything in Freemium
Advanced search
Find every technique, tactic and procedure (TTP) for every report, actor, malware, tool & campaign
Full Mitre Att&ck TTP context from every report, down to the page
Entity Level Mitre Att&CK heatmaps
Professional
RECOMMENDED
For security professionals ready to focus on threats that matter.
Features
Everything in Community
5 Constellations™
Evidence-Based Heat Maps
Attack Path Generator
Automated Alerts
Limited Playbook Executions (5 per month)
Limited API Usage
Early Access to Premium Feature Releases
Enterprise
For enterprise teams desiring threat-informed defense without overhead.
Features
Everything in Professional
Unlimited Users
Unlimited Playbook Executions
Unlimited API Usage
Vendor Integrations
Dedicated Support
Early Access to Premium Feature Releases
Turn Intelligence Into Threat-Informed Defense.
Be among the first to experience relevant, evidence-backed outcomes — no overhead, no complexity.